According to Paul Moore (IT consultant and tech enthusiast ) was able to found a Major XSRF or Cross Site Request Forgery exploit which allow a hacker to hijack eBay account and can use it for bidding illegally.
Paul found the vulnerability in page which users use to update their profile and that’s because the field which links it to the user’s active cookie is missing.
This allows a hacker to submit the form with pre-populated data which doesn’t affect the user password directly but can indirectly as it allows a hacker to change the information that is used to reset the password.
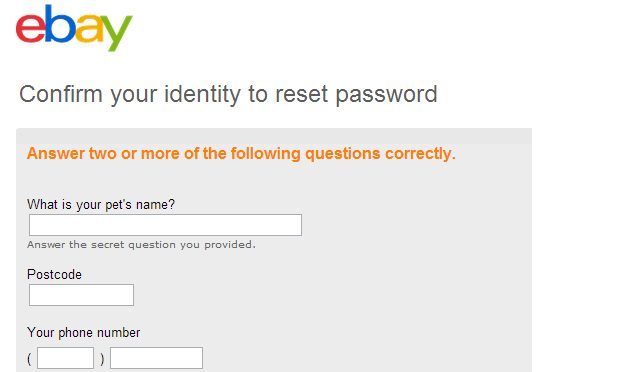
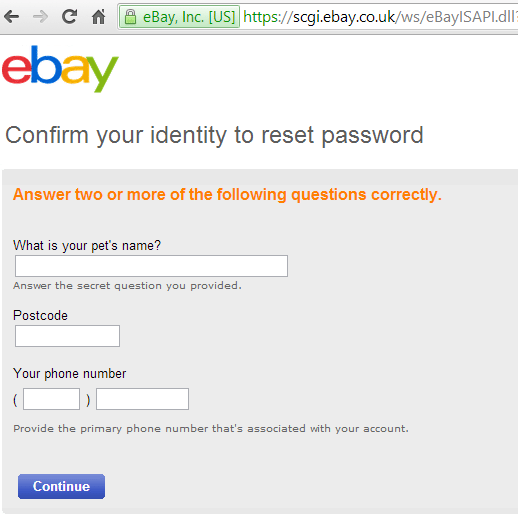
After this attacker simply needs to submit his own phone number and postal code- the information needed at the time of resetting the password.
Now the main phenomenon starts, after the submission of phone number, postal code- eBay gives an option to confirm that you really owned the account in which it sends the four-digit confirmation code to phone number instead of an email address, it uses that phone number which Paul had entered earlier, Now your account got hacked by a hacker easily in only 1 minute.
From a Hacked eBay account:
- The hacker can now place orders without needing to know your PayPal username or password.
- The hacker can’t steal funds directly from your PayPal account (or associated bank account), but they can start bidding/buying on your behalf. Before you know it..
- The hacker can put a fictitious item up for sale (with a “Buy It Now” price) and bid for it from the victim’s account.
According to Paul, the main cause of vulnerability- on eBay you may login over SSL, but subsequent pages are delivered over HTTP. That is not secure.
Paul reported this vulnerability to eBay on August 5, officials responded him and promised to address the issue.
However, 43 days later, the flaw is still present. The expert told Softpedia that he checked the website once again.
On September 2, Moore attempted to get a status update, but eBay representatives informed him that they didn’t provide updates until the vulnerability was repaired.
You can follow a detailed report by Paul on his blog, also check out the demonstration video provided by Paul: